WordPress and Suricata, The Test
Adding a full featured IDPS solution like Suricata is a good step in protecting any Web based application like WordPress, but how well will it fare when under attack?
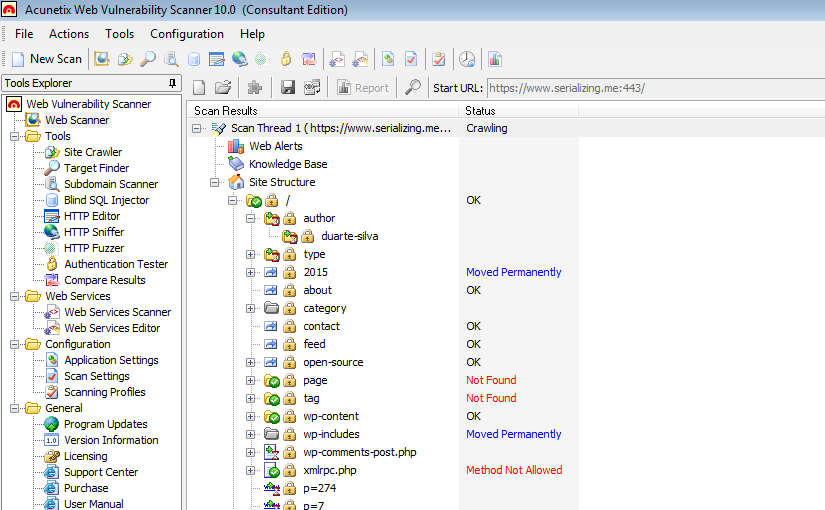
To answer this question, one has to account for the quality of both the rules and the vulnerability scanner used. For the rules, two sets were used, the Emerging Threats Pro and the Emerging Threats Open ruleset. Acunetix Web Vulnerability Scanner (WVS) was used to perform the vulnerability scan, even though it is not one of the best scanners in the market, it does fair quite well. The test were executed under the following scenarios:
- No protection (first run, baseline)
- Suricata with Emerging Threats:
- Open Ruleset (second run)
- Pro Ruleset (third and last run)
In all scenarios, the Acunetix scan was configured with the default scanning profile targeting a Enterprise Linux based host with PHP installed. The WordPress version is 4.2.2 and no plug-ins are installed. The rule files used from the Open Ruleset were the same as with the Pro Ruleset. There is only a difference in the filename, in the Open Ruleset it starts with emerging-* but in the Pro Ruleset it does not.
1rule-files:
2 - emerging-attack_response.rules
3 - emerging-current_events.rules
4 - emerging-dns.rules
5 - emerging-dos.rules
6 - emerging-exploit.rules
7 - emerging-policy.rules
8 - emerging-rpc.rules
9 - emerging-scan.rules
10 - emerging-shellcode.rules
11 - emerging-sql.rules
12 - emerging-user_agents.rules
13 - emerging-web_server.rules
14 - emerging-web_specific_apps.rules
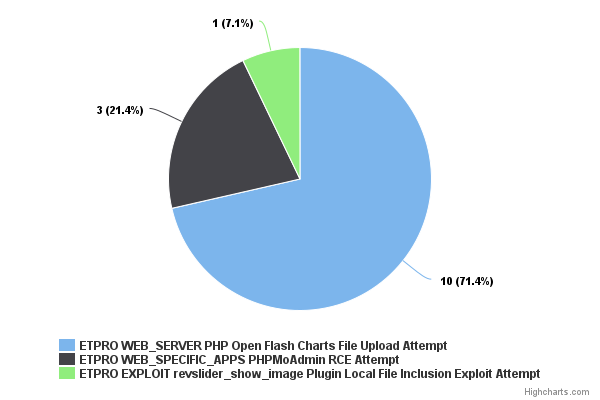
There is an extra 52 alerts using the Emerging Threats Pro rules. From this 52, only 14 are generated by Pro only rules were the other 38 are generated by rules that are also present in the Open Ruleset and were simply alerted in greater number in the third run.
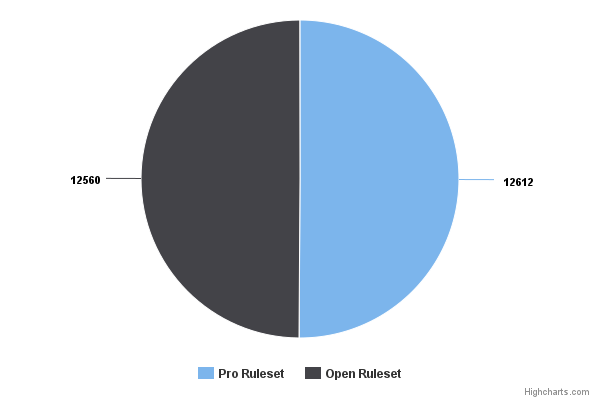
In total the Acunetix scan with the rules that were used (downloaded 6 of July at 15:26) generated 12612 alerts with the Pro rules and 12560 for the Open rules. It is then possible to conclude that there isn’t much difference between the Pro and the Open Ruleset when it comes to vulnerability scans performed by Acunetix WVS (and possibly also against other scanners).
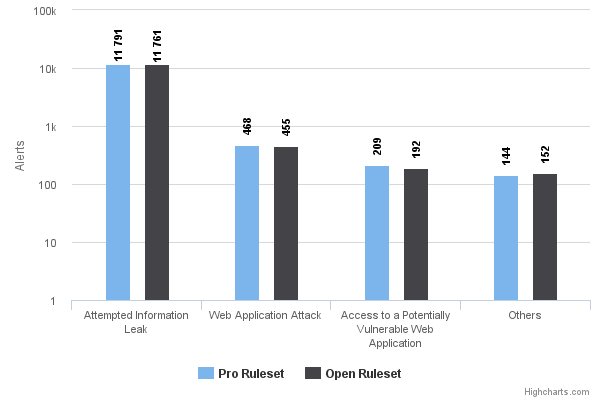
The breakdown of the alert categories is pretty even and differences are almost negligible if we take into account the range of the numbers involved.
Acunetix reported 1 high, 2 medium and 27 low risk vulnerabilities. Out of those, the only ones that were related with WordPress and that could be actionable (read, no false positives) against the WordPress installation is 1 medium and 1 low risk vulnerabilities.
- Medium risk
- WordPress XML-RPC authentication brute-force
- Low Risk
- Login page password-guessing attack
All of them would have been mitigated by Suricata (independently of the rule set used) by the following rules.
ET WEB_SERVER WordPress Login Bruteforcing DetectedET SCAN Possible WordPress xmlrpc.php BruteForce in Progress
In conclusion, Suricata faired extremely well in terms of performance and security/protection alerting to attacks that ranged from SQL injection to known vulnerabilities in WordPress plugins.
One thing to notice though, was that the second and third test runs were executed with Suricata in IDS mode, otherwise the scan would take too long. A scan of the target took on average one hour and an half without Suricata or with Suricata in IDS mode, if Suricata is configured in IPS mode, the scan would take more than six hours and by that time, it wouldn’t even be close to half way done (timeout was set to 5 seconds). An added reason for running Suricata, it will frustrate the more impatient attackers :D