Posts Archived Under "Linux"

Raspberry Pi Custom Fedora Kernel
Over the years I have gotten very used to Red Hat Enterprise Linux (RHEL) type distributions, and have for a long time now selected Fedora as my default goto Linux distribution. However, I needed a specific driver that comes out of the box with Raspbian (Raspberry Pi’s Debian based distribution), but does not come with Fedora. This post elaborates how to go about compiling a custom kernel on a Pi running Fedora.
Read More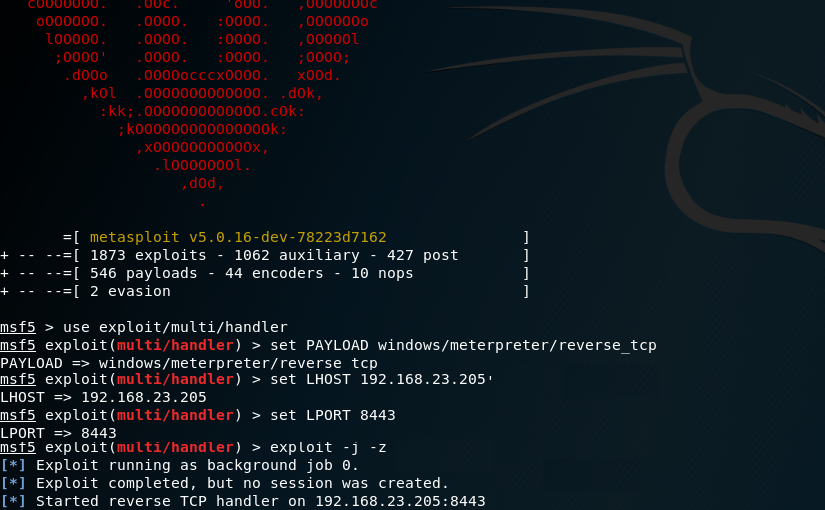
Simulating APTs For Fun
In the post I will explain how one could simulate an Advanced Persistent Threat (APT) using Praetorian’s Purple Team Attack Automation and MITRE’s ATT&CK framework.
Read More
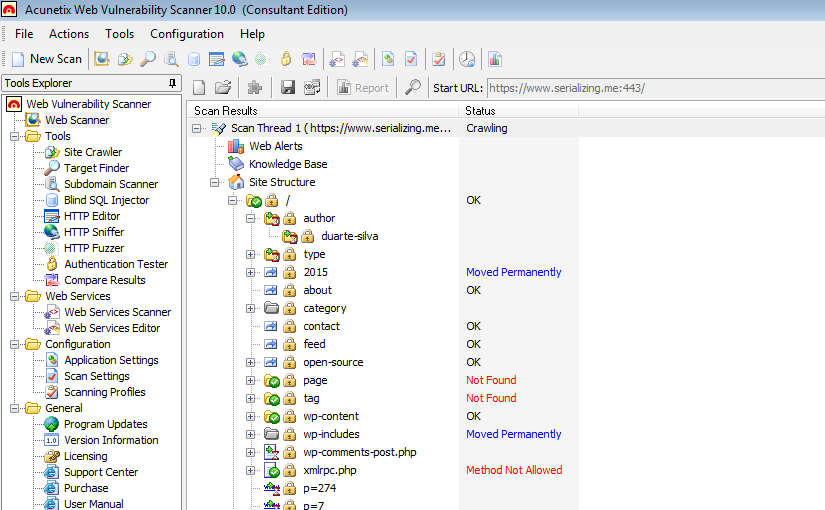
Reversing the TC7210 Embedded Linux Firmware
In this article I will explain how to reverse the firmware of the embedded Linux part of the Technicolor (TC) 7210 router by leveraging the usual tools of the trade.
Read More
Rooting the Technicolor 7210
The Technicolor 7210 home router is a powerful little device. It provides 1Gbps Ethernet, dual-band wireless for speeds ranging from 300Mbps to 1300Mbps, and Network Attached Storage (NAS) for file sharing and media streaming.
Read More
Migrated From WordPress to Hugo
I have been using WordPress since I started blogging, but since then, the blogging landscape changed a lot. Welcome to the age of static site generators.
Read More
Reversing Aruba Instant Firmware
Aruba produces two different software loads for their Access Point hardware. The first is called ArubaOS and the second is called Aruba Instant. With ArubaOS, the AP requires a Mobility Controller (hardware) to be installed in the network. With the Aruba Instant it is possible to run AP’s independently (standalone mode) or in a cluster, with no Mobility Controller in the network.
What follows is the full process to extract all the files recreating the Aruba Instant firmware file system.
Read More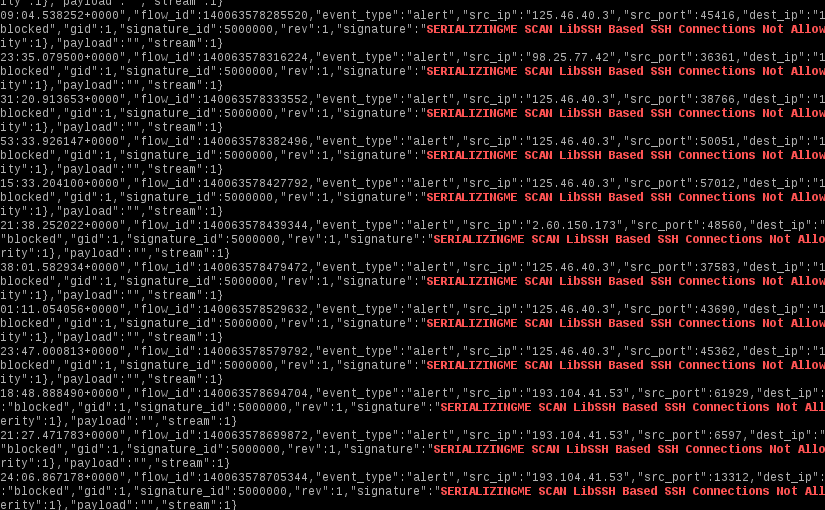
SSH Brute Force and Suricata
Since SSH is one of the most pervasive ways to manage servers remotely, it is also one of the most plagued by brute force attacks. What follows is a simple set of Suricata rules to stop the majority of SSH brute force attacks. It will drop connections based on the reported SSH client version.
Read More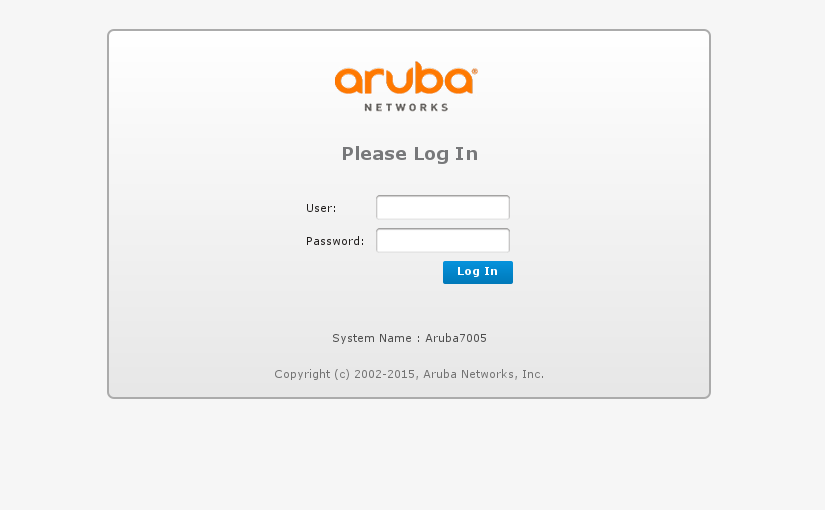
Reversing ArubaOS Firmware
Some time ago, I had the chance to get my hands on a ArubaOS firmware, what follows is the full process to extract all the files recreating the appliance running file system. This had the objective of fuzzing the extracted binaries in QEMU (ArubaOS management console is CGI based).
Read More