Posts
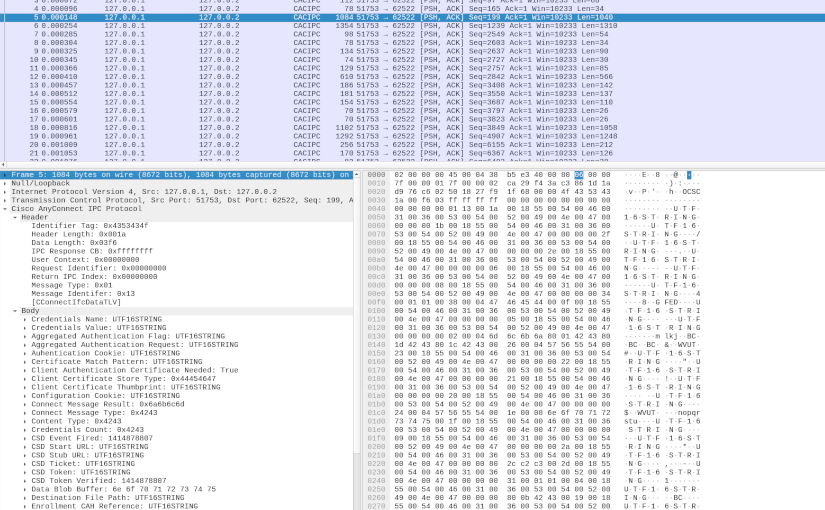
AnyConnect Inter-Process Communication
In my first deep dive into Cisco AnyConnect (CAC) Secure Mobility Client (see AnyConnect Elevation of Privileges Part 1 and Part 2), I reversed engineered how CAC made use of a TCP based Inter-Process Communication (IPC) protocol. Based on that research, I found a Local Privilege Escalation (LPE) vulnerability (see CVE-2016-9192 and the proof-of-concept code). Yorick Koster and Antoine Goichot followed suit, and using that research also found other vulnerabilities (see CVE-2020-3153, CVE-2020-3433, CVE-2020-3434, and CVE-2020-3435). This post presents the results of my second deep dive, correcting a wrong conclusion about the protocol, further reverse engineering the various IPC messages, and providing some tools that can potentially aid further research.
Read More
Freedom and Solitude
The freedom of not having to account for someone else's needs, wants and feelings, has the cost of solitude.
Image via Pexels @ Pixabay

Raspberry Pi Custom Fedora Kernel
Over the years I have gotten very used to Red Hat Enterprise Linux (RHEL) type distributions, and have for a long time now selected Fedora as my default goto Linux distribution. However, I needed a specific driver that comes out of the box with Raspbian (Raspberry Pi’s Debian based distribution), but does not come with Fedora. This post elaborates how to go about compiling a custom kernel on a Pi running Fedora.
Read More
e-GPU Plus Bracket
Razer Core X Chroma is an excellent device, but its functionalities didn’t fully cover my use case. As such, I decided to add a bracket and a PCI-e extender to the mix.
Read More
Bypass All The GPOs
During a red team engagement, one has landed on a machine with the need to make an application “ignore” Group Policies enforced configurations. This application runs on the context of the user but the settings are only changeable with administrative privileges and without access to a highly privileged account how can one make the application ignore these settings?
Read More
Simulating APTs For Fun
In the post I will explain how one could simulate an Advanced Persistent Threat (APT) using Praetorian’s Purple Team Attack Automation and MITRE’s ATT&CK framework.
Read More
Reversing the TC7210 Embedded Linux Firmware
In this article I will explain how to reverse the firmware of the embedded Linux part of the Technicolor (TC) 7210 router by leveraging the usual tools of the trade.
Read More