Posts Archived Under "Windows"

Bypass All The GPOs
During a red team engagement, one has landed on a machine with the need to make an application “ignore” Group Policies enforced configurations. This application runs on the context of the user but the settings are only changeable with administrative privileges and without access to a highly privileged account how can one make the application ignore these settings?
Read More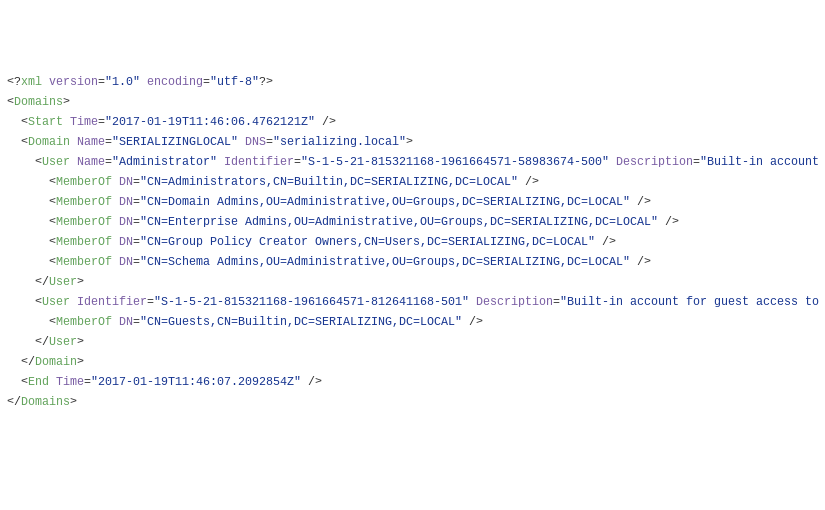
PowaScripts Update: Kerberos Pre-authentication
After reading harmj0y blog post about “Roasting AS-REPs”, I have decided to update the Dump-User.ps1 script in order for it to report on users that don’t have Kerberos pre-authentication enabled. Running the updated version against a “in the wild” target yielded interesting results to say the least.
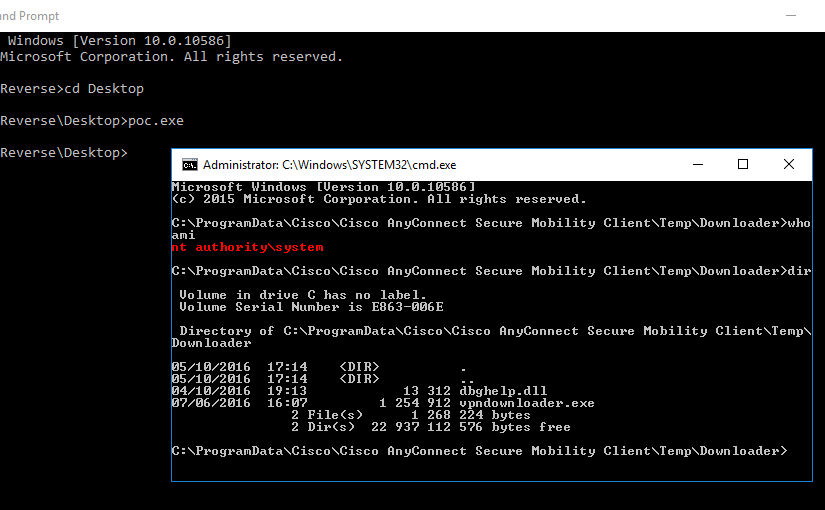
AnyConnect Elevation of Privileges, Part 2
In the previous part of this multi-part article, I explained how I reversed engineered one of the binaries of the Cisco AnyConnect (CAC) Secure Mobility Client. This allowed me to understand the header format of the network packets used in the Inter-Process Communication (IPC) mechanism. In this part, I will focus on doing a more dynamic analysis in order to understand what goes in the packet body.
Read More
AnyConnect Elevation of Privileges, Part 1
The Cisco AnyConnect (CAC) Secure Mobility Client doesn’t have the brightest security track record. CVE-2015-4211 and CVE-2015-6305 are only two out of the fourteen CVEs that have been assigned to it just in 2015. This spiked my curiosity and prompted me to confirm if Cisco had properly fixed the underlying issue of these vulnerabilities.
Read More
HPQPswd Encrypted Passwords Decryption
Ever wondered how to decrypt HPQPswd encrypted passwords? So did I when, for the first time, I came across a strange file called password.bin with a magic value of _HPPW12_.
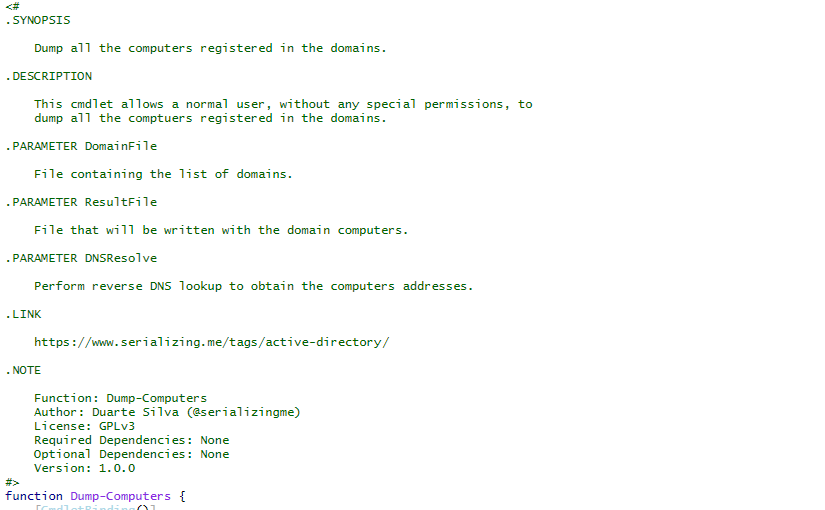
Active Directory Dump
During many penetration tests (or red versus blue team exercises), I have found myself with the need to investigate users, groups, computers and policies of a Windows domain. To do that, I have developed a series of PowerShell scripts that dump all that information from Active Directory into XML files.
Read More
Titan Quest Invincibility Cheat
In the last level of Titan Quest, every player will have to face the titan Typhon, Bane of the Gods. A task that is very far from easy…
Read More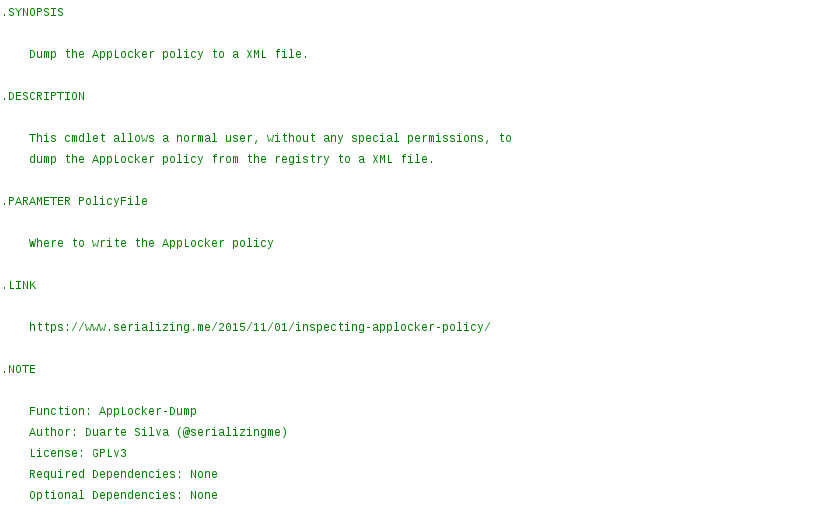
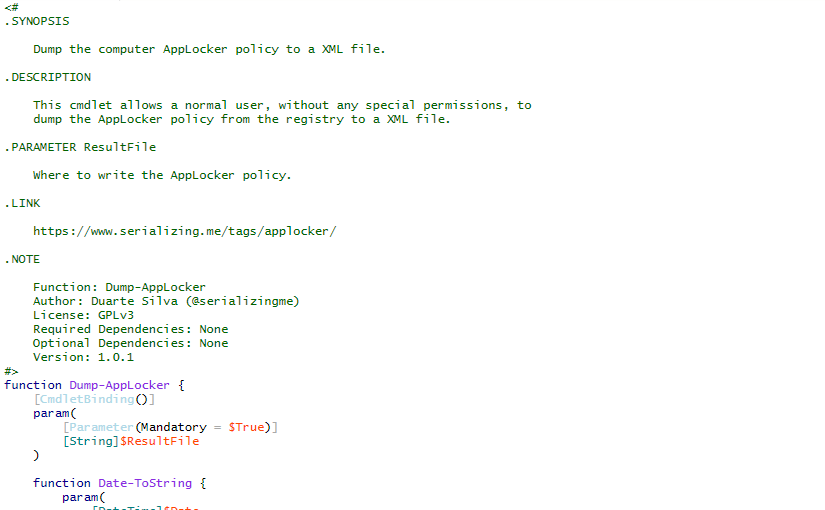
Inspecting AppLocker Policy
While doing incident response, if AppLocker is being used but the computer still got infected by a malicious executable, it is useful to know exactly what AppLocker policy is currently applied.
Read More