Posts Archived Under "Network"
AnyConnect Inter-Process Communication
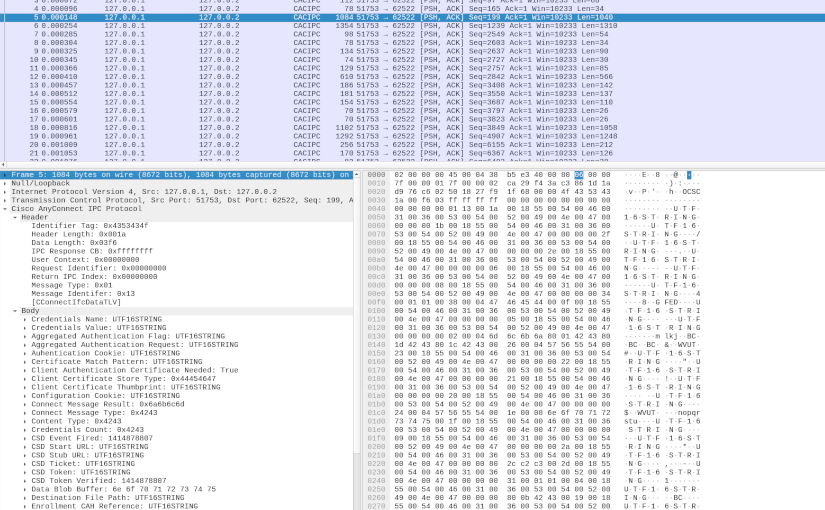
In my first deep dive into Cisco AnyConnect (CAC) Secure Mobility Client (see AnyConnect Elevation of Privileges Part 1 and Part 2), I reversed engineered how CAC made use of a TCP based Inter-Process Communication (IPC) protocol. Based on that research, I found a Local Privilege Escalation (LPE) vulnerability (see CVE-2016-9192 and the proof-of-concept code). Yorick Koster and Antoine Goichot followed suit, and using that research also found other vulnerabilities (see CVE-2020-3153, CVE-2020-3433, CVE-2020-3434, and CVE-2020-3435). This post presents the results of my second deep dive, correcting a wrong conclusion about the protocol, further reverse engineering the various IPC messages, and providing some tools that can potentially aid further research.
Read More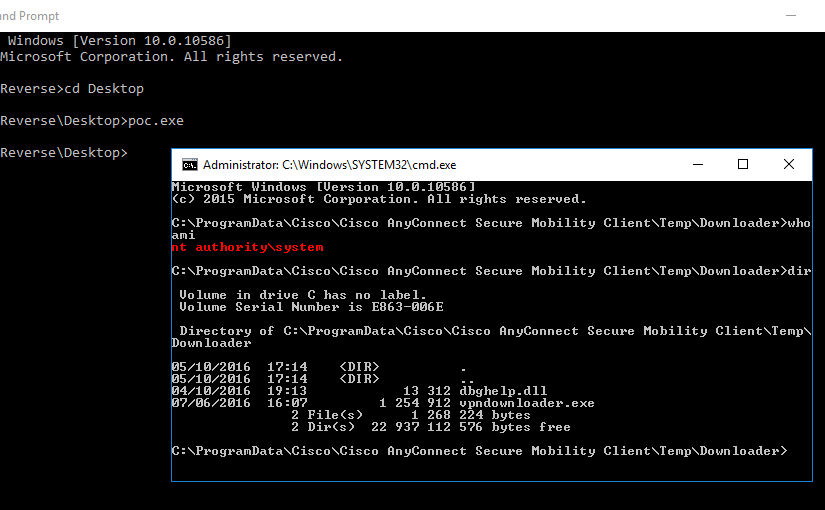
AnyConnect Elevation of Privileges, Part 2
In the previous part of this multi-part article, I explained how I reversed engineered one of the binaries of the Cisco AnyConnect (CAC) Secure Mobility Client. This allowed me to understand the header format of the network packets used in the Inter-Process Communication (IPC) mechanism. In this part, I will focus on doing a more dynamic analysis in order to understand what goes in the packet body.
Read More
AnyConnect Elevation of Privileges, Part 1
The Cisco AnyConnect (CAC) Secure Mobility Client doesn’t have the brightest security track record. CVE-2015-4211 and CVE-2015-6305 are only two out of the fourteen CVEs that have been assigned to it just in 2015. This spiked my curiosity and prompted me to confirm if Cisco had properly fixed the underlying issue of these vulnerabilities.
Read More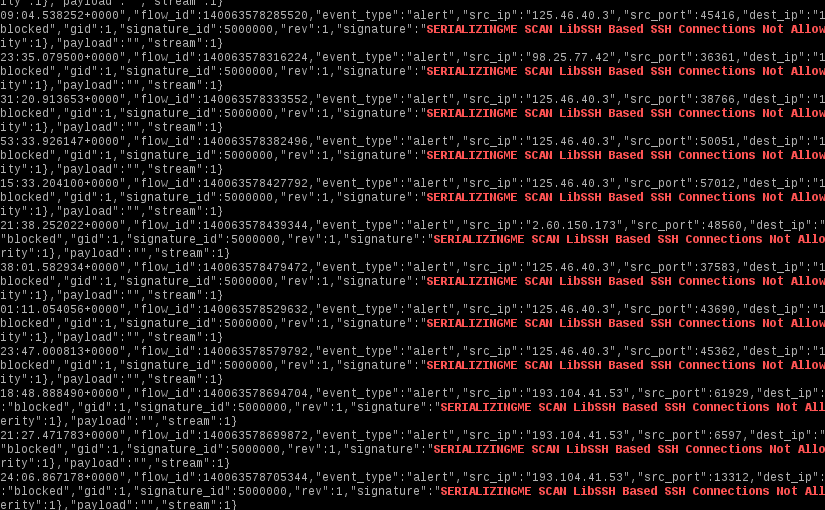
SSH Brute Force and Suricata
Since SSH is one of the most pervasive ways to manage servers remotely, it is also one of the most plagued by brute force attacks. What follows is a simple set of Suricata rules to stop the majority of SSH brute force attacks. It will drop connections based on the reported SSH client version.
Read More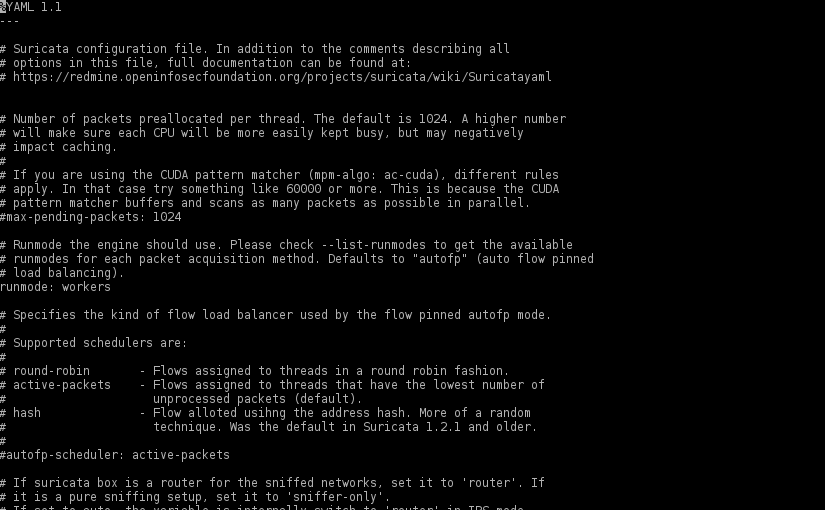
Protecting WordPress with Suricata
There aren’t any silver bullets that will protect a WordPress installation against every single attack, but adding a full featured IDPS solution like Suricata, is a good step in protecting not only that “all too many times vulnerable” WordPress installation but also other services like SSH.
Read More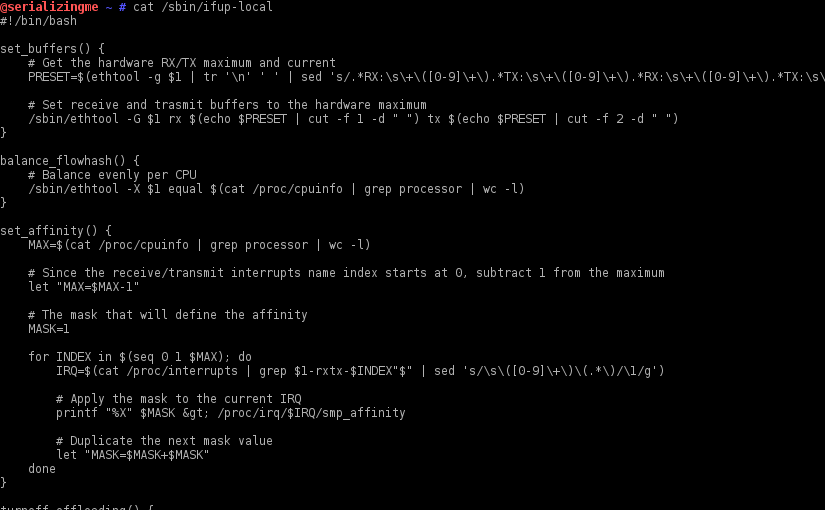
RX/TX Buffers, Flow Hash and Others on Boot
After installing Suricata, some fine tuning of the network interface(s) used in the traffic capture is required to ensure every ounce of performance is extracted from the new IDPS installation. Those configurations need to be persisted when the system is power cycled. To do that on a Enterprise Linux based OS (e.g. RedHat, CentOS, Fedora, etc.) one can leverage the /sbin/ifup-local script.