Posts Archived Under "Configuration"

Raspberry Pi Custom Fedora Kernel
Over the years I have gotten very used to Red Hat Enterprise Linux (RHEL) type distributions, and have for a long time now selected Fedora as my default goto Linux distribution. However, I needed a specific driver that comes out of the box with Raspbian (Raspberry Pi’s Debian based distribution), but does not come with Fedora. This post elaborates how to go about compiling a custom kernel on a Pi running Fedora.
Read More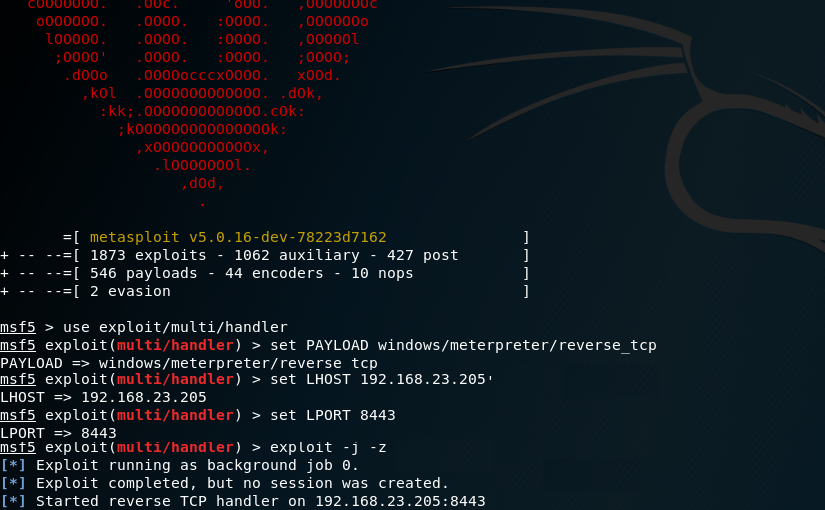
Simulating APTs For Fun
In the post I will explain how one could simulate an Advanced Persistent Threat (APT) using Praetorian’s Purple Team Attack Automation and MITRE’s ATT&CK framework.
Read More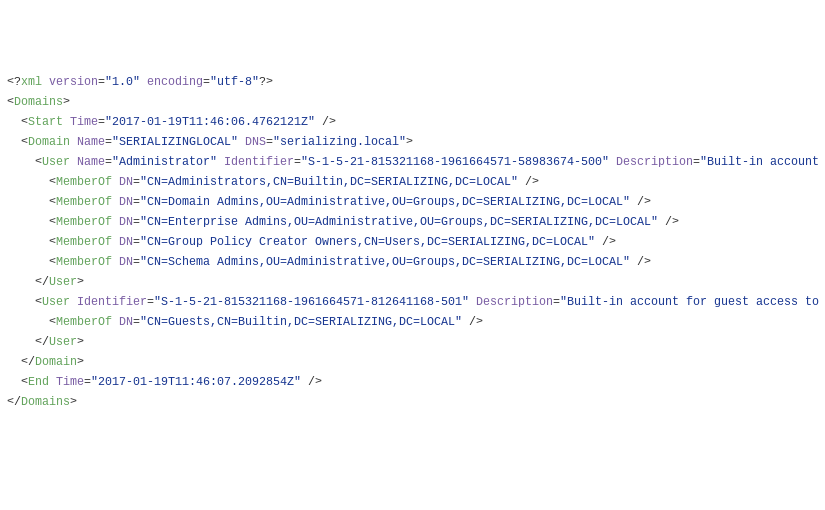
PowaScripts Update: Kerberos Pre-authentication
After reading harmj0y blog post about “Roasting AS-REPs”, I have decided to update the Dump-User.ps1 script in order for it to report on users that don’t have Kerberos pre-authentication enabled. Running the updated version against a “in the wild” target yielded interesting results to say the least.
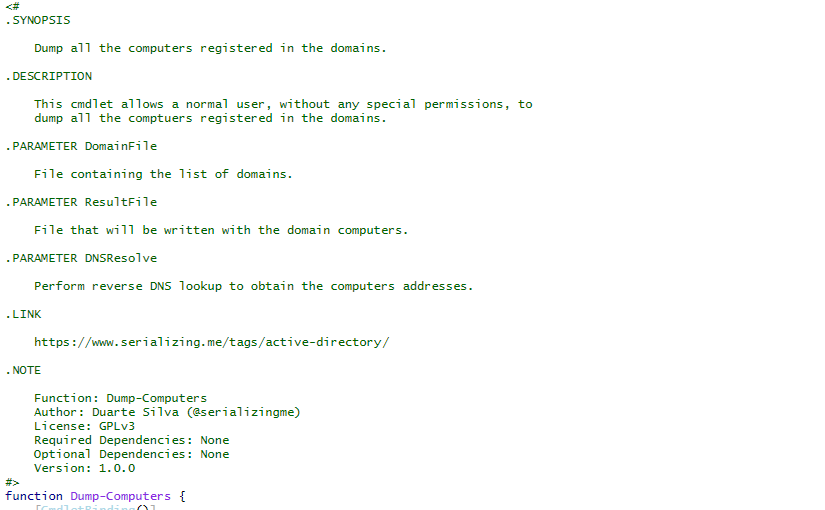
Active Directory Dump
During many penetration tests (or red versus blue team exercises), I have found myself with the need to investigate users, groups, computers and policies of a Windows domain. To do that, I have developed a series of PowerShell scripts that dump all that information from Active Directory into XML files.
Read More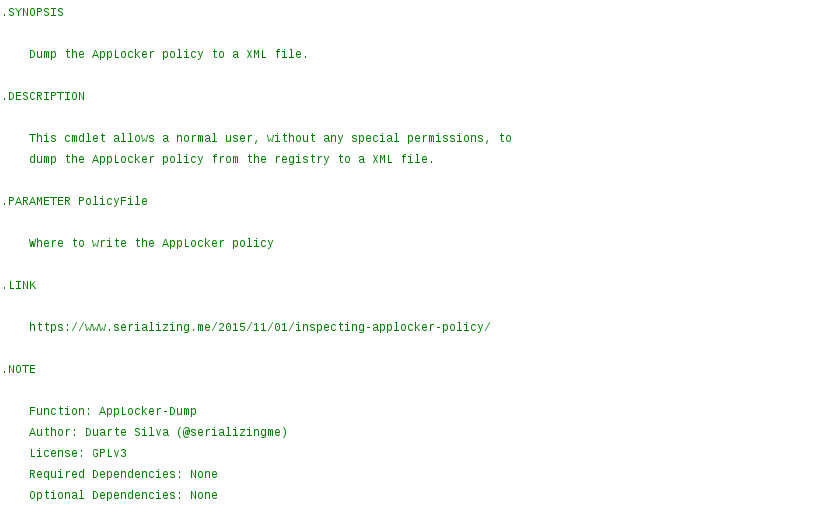
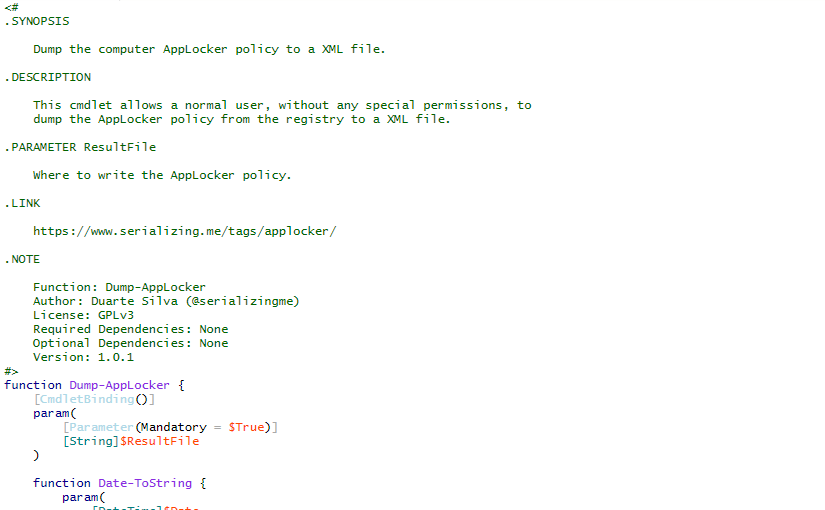
Inspecting AppLocker Policy
While doing incident response, if AppLocker is being used but the computer still got infected by a malicious executable, it is useful to know exactly what AppLocker policy is currently applied.
Read More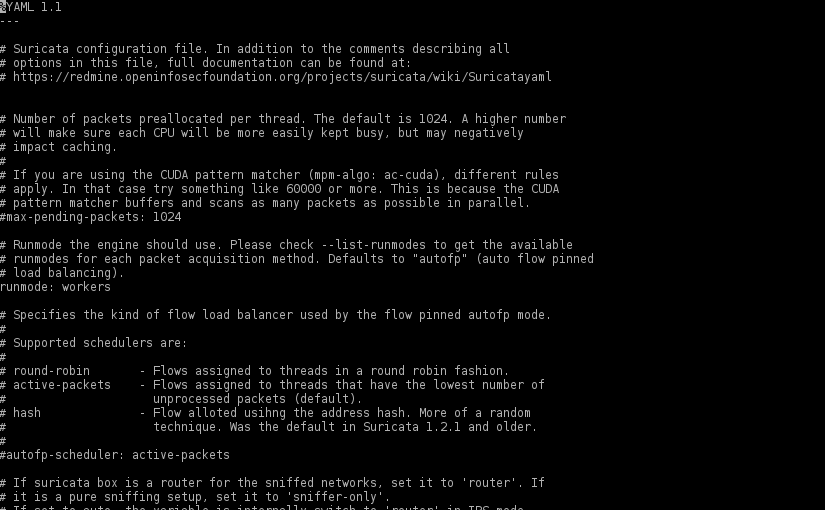
Protecting WordPress with Suricata
There aren’t any silver bullets that will protect a WordPress installation against every single attack, but adding a full featured IDPS solution like Suricata, is a good step in protecting not only that “all too many times vulnerable” WordPress installation but also other services like SSH.
Read More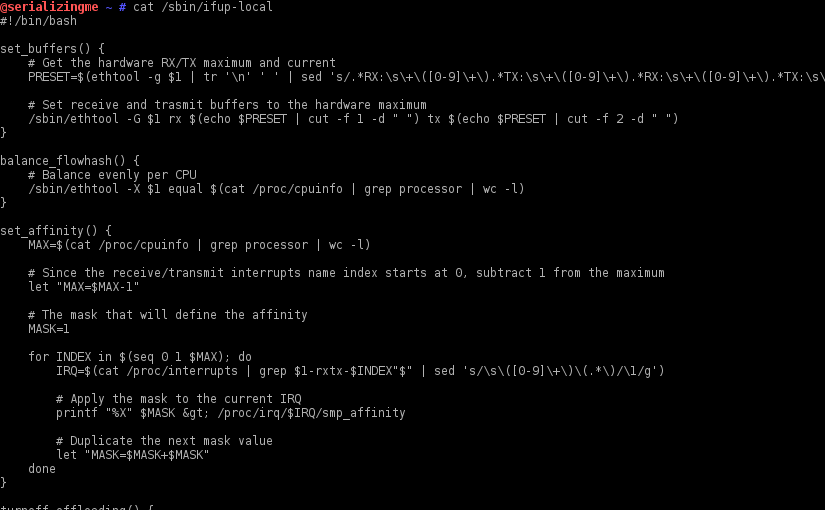
RX/TX Buffers, Flow Hash and Others on Boot
After installing Suricata, some fine tuning of the network interface(s) used in the traffic capture is required to ensure every ounce of performance is extracted from the new IDPS installation. Those configurations need to be persisted when the system is power cycled. To do that on a Enterprise Linux based OS (e.g. RedHat, CentOS, Fedora, etc.) one can leverage the /sbin/ifup-local script.