Portuguese Banking Apps, Yay or Nay?
I have been using my bank mobile application for a while, but never had a look at its security. This is an account of my findings, not only on that specific application, but on eight of the offerings available in the Portuguese market.
I have focused my research in one of the most important aspects of any type of banking applications, how secure are the communications with the bank systems (API endpoints). In simple terms, how hard would it be for a threat actor to intercept and subsequently decrypt the mobile application communications in order to impersonate the user.
- ActivoBank and Millennium (same base application and endpoint)
- Banco Popular
- Barclays
- BPI App (Banco Português de Investimento)
- Caixadirecta (Caixa Geral de Depósitos, CGD)
- NBapp (Novo Banco)
- Santander Totta
What follows is the grade of resilience against attack by both the endpoint, and the application of each bank. The higher the grade (being A+ the best, and F the worst), the harder is for a threat actor to successfully attack the communications.
| Bank | Points | Grade | |
|---|---|---|---|
| Endpoint | Application | ||
| Barclays | 2,267 | 1 | A |
| CGD | 2,367 | 1,5 | A- |
| Santander Totta | 1,833 | 2 | A- |
| ActivoBank | 1,833 | 2 | A- |
| Millennium | |||
| BPI | 2,233 | 2 | B |
| Novo Banco | 2,267 | 2 | B |
| Banco Popular | 6 | 5,5 | F |
Starting from the top, the Barclays endpoint could improve in three points, uses a weak signature algorithm, still supports weak cipher suites and doesn't support forward secrecy. The application on the other hand, couldn't do it any better, since it is pinning the certificate that the server should present. That renders man-in-the-middle (MiTM) attacks impossible.
The CGD endpoint could improve in two points, only supports TLS 1.0 and doesn't support forward secrecy. The application does certificate pinning, but only to the level of the root certificate authority.
With the same exact points, both in the endpoint and in the application, Santander Totta, ActivoBank and Millennium can improve by deploying better forward secrecy support, enabling TLS downgrade prevention, increase the cipher suite strength, and add certificate pinning to the application.
BPI and Novo Banco, have in common weak cipher suites, no forward secrecy and no certificate pinning. Novo Banco could also improve by increasing the signature algorithm strength while BPI could improve by supporting TLS versions higher than 1.0 and prevent TLS downgrade.
The worst of the test, was Banco Popular, both in the endpoint and in the application. The endpoint is vulnerable to POODLE, supports the Export algorithms (very insecure), TLS only goes up to version 1.0, supports both SSL 2 and SSL 3 (both vulnerable to all sorts of attacks), does not support forward secrecy and does not prevent TLS downgrade.
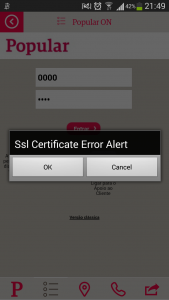
In the application, there is validation of the certificate presented by the endpoint, but the application ask if the user wants to continue, leaving to the user the choice to continue over an insecure connection (most users will do the wrong choice!). Anyone using this application, is risking a bank account compromise and consequently, financial loss. The verdict is to stay clear from using it!
There is still a lot of room for improvement, but overall, it was a nice surprise to verify that almost all the applications fared quite well on the tests.