Curious Fish is Curious
Testing virtualized malware sandboxes with Paranoid Fish wasn’t enough, there might be other things that could be improved to avoid malware detection. Enter Curious Fish, a tool to help fingerprinting sandboxes.
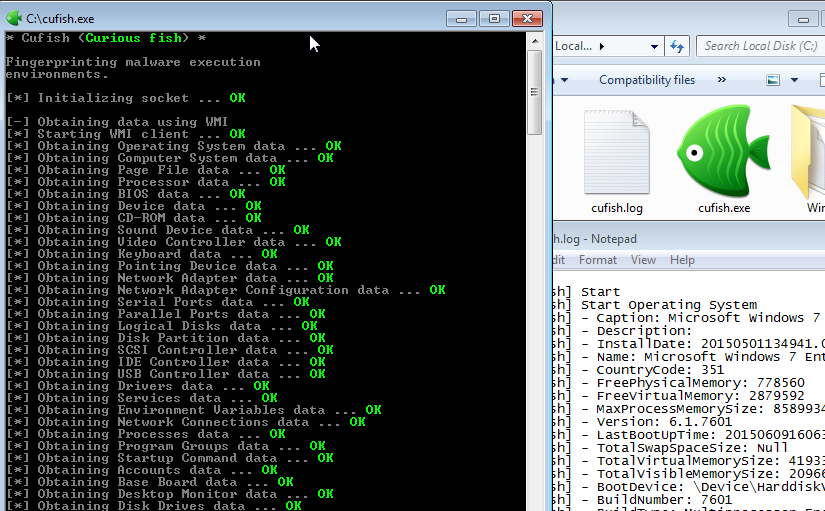
These types of environments need to be stealth, being able to avoid detection by malware is a must because it will spare the researcher or incident responder precious time in the analysis of the incident. Marking a fingerprinting behaviour as malicious is useful, but prone to some false positives and in the end, when you have hundreds (to thousands) of incidents to deal with, you’ll want a system that is able to run the samples to the full of their functionality so that you don’t have to. Curious Fish (Cufish) aims to help with that, providing information about the execution environment that could be used to pre-emptively improve the sandbox and avoid detection by malware. Cufish leverage Windows Management Instrumentation (WMI) to obtain information about:
- Operating System
- Processor
- BIOS
- Hardware devices
- Partitions
- Environment variables
- Network connections and interfaces
- Peripherals
- Software
There were two challenges, the first, was that MinGW doesn’t play well with OLE and C++, after various attempts, the solution was to drop C++ and develop the WMI client code in pure C. The second challenge was related with how the information generated by Cufish would be exposed to the user as all the tested sandbox products (commercial or free) don’t allow for files created by the sample to be downloaded.
The solution was to open a UDP socket (doesn't require a server listening on the other end), pointing to a local network IP address that is (most likely) different from any IP address that the sandboxes use (forcing the traffic to exit the virtual machine). This will suffice, because many of the sandboxes allow for packet dumps to be downloaded. In the ones that don't, the only option is to check the output of the dependency walker.
After executing Cufish in various systems, follows a summary of some common tell-tale signs (compared against a physical machine to avoid false positives).
| Sign | Sandbox Based on | |||
|---|---|---|---|---|
| VMWare | V.Box | QEMU | ||
| Virtual Machine Bus Driver | No | No | Yes | |
| CPU/Chipsets miss match | No | No | Yes | |
| References to Virtualization | Model | Yes | Yes | No |
| OEM | Yes | Yes | No | |
| BIOS | Yes | Yes | No | |
| Hardware | Yes | Yes | No | |
There is still a lot of information (specially on the hardware/drivers side like device identifiers and such) that needs to be spoofed/hidden in order to improve stealthiness. All of them are easy to do so, since they will be accessed using the Windows registry or by calling API’s.
The code can be found in this pull request or in this branch.