Posts

Facts and Alternative Realities
(...) simply insisted we prove that the Queen didn’t do it — that is, demanding a refutation of wild speculation to prove fact, rather than seeking out the evidence first. This proof-by-negation is akin to fastidiously believing in the tooth fairy simply because no one has seen proof that the tooth fairy doesn’t exist. That is noxious thinking — and, (...), it’s exactly the kind of aggressive, close-minded speculation that fuels fake news, Trumpian rhetoric, and political divisions.
This post isn’t about politics, it’s about how easy it is to fall in the fallacy of proving something didn’t happen by negating it. It’s about how tiresome it can be to always fact check, proving through facts what is reality and what is fiction. It’s about avoiding a dark universe of alternative realities that enclose you in an existence of self-feeding bigotry. Of believing your feelings are facts, are reality.
Image via StockSnap @ Pixabay

Rooting the Technicolor 7210
The Technicolor 7210 home router is a powerful little device. It provides 1Gbps Ethernet, dual-band wireless for speeds ranging from 300Mbps to 1300Mbps, and Network Attached Storage (NAS) for file sharing and media streaming.
Read More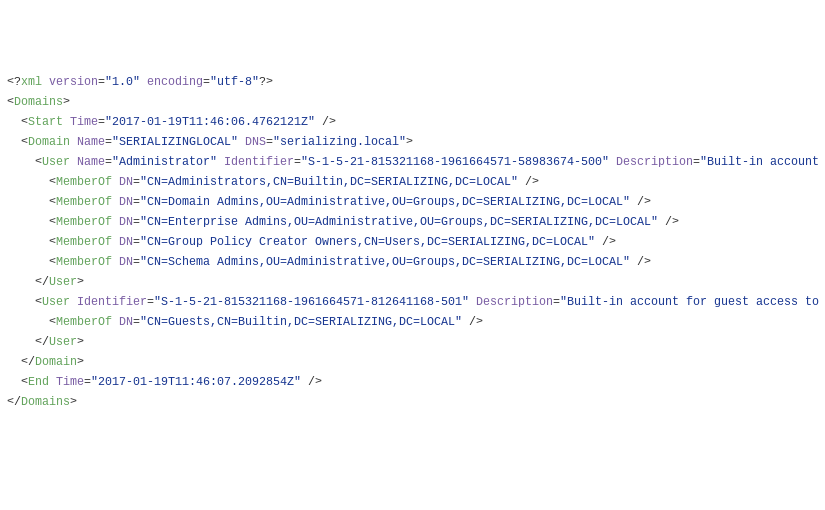
PowaScripts Update: Kerberos Pre-authentication
After reading harmj0y blog post about “Roasting AS-REPs”, I have decided to update the Dump-User.ps1 script in order for it to report on users that don’t have Kerberos pre-authentication enabled. Running the updated version against a “in the wild” target yielded interesting results to say the least.
AnyConnect Elevation of Privileges, Part 2
In the previous part of this multi-part article, I explained how I reversed engineered one of the binaries of the Cisco AnyConnect (CAC) Secure Mobility Client. This allowed me to understand the header format of the network packets used in the Inter-Process Communication (IPC) mechanism. In this part, I will focus on doing a more dynamic analysis in order to understand what goes in the packet body.
Read More
AnyConnect Elevation of Privileges, Part 1
The Cisco AnyConnect (CAC) Secure Mobility Client doesn’t have the brightest security track record. CVE-2015-4211 and CVE-2015-6305 are only two out of the fourteen CVEs that have been assigned to it just in 2015. This spiked my curiosity and prompted me to confirm if Cisco had properly fixed the underlying issue of these vulnerabilities.
Read More
HPQPswd Encrypted Passwords Decryption
Ever wondered how to decrypt HPQPswd encrypted passwords? So did I when, for the first time, I came across a strange file called password.bin with a magic value of _HPPW12_.
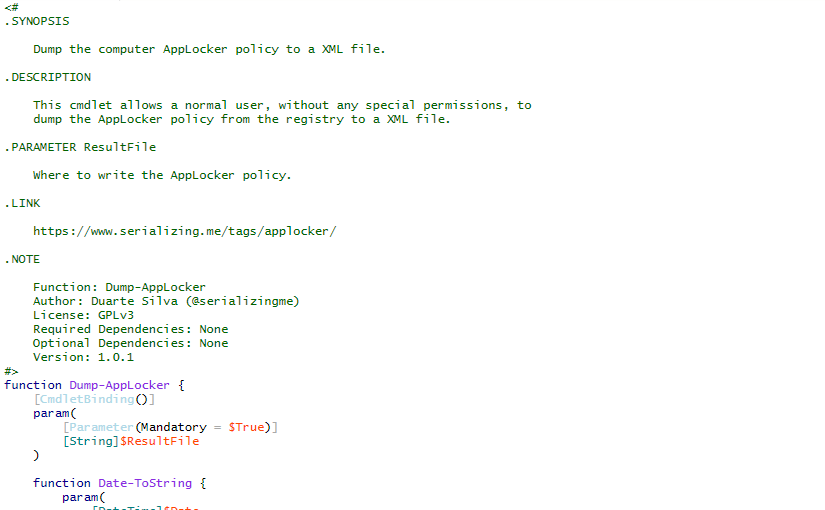
Active Directory Dump
During many penetration tests (or red versus blue team exercises), I have found myself with the need to investigate users, groups, computers and policies of a Windows domain. To do that, I have developed a series of PowerShell scripts that dump all that information from Active Directory into XML files.
Read More
Migrated From WordPress to Hugo
I have been using WordPress since I started blogging, but since then, the blogging landscape changed a lot. Welcome to the age of static site generators.
Read More
Portugueses e Senhas de Acesso, Um Caso de Estudo
Nos últimos anos tenho tido a oportunidade de coleccionar várias listas de senhas de acesso. O que se segue é um caso de estudo focado em três dessas listas. Sendo que estas, são de sítios portugueses.
Read More